Hi
-
1 BSP environment:
TX2 jetpack 4.6 L4T R32.6.1 kernel 4.9 aarch64
TX2 (p3310) -
2 background:
now we are preparing for the coming mass production of our project. So, we want to increase efficiency, and help manufacture update FW more easily. -
3 issues:
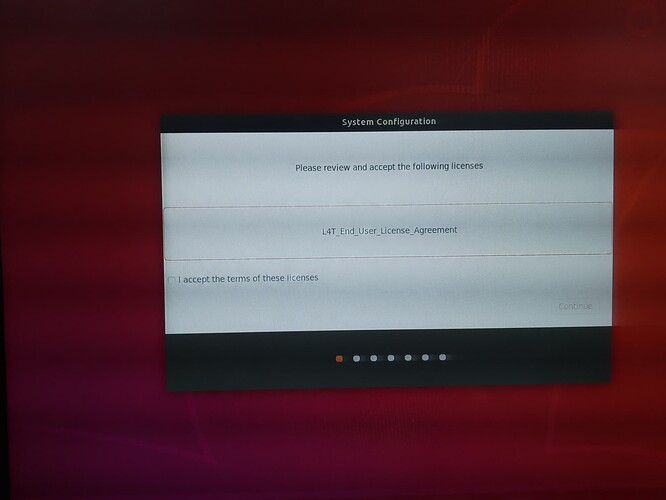
3.1 after we flashing a brand new tx2, when the device bring up at first time, we have to do system configuration, such as time zone, key board config, and account name and password, etc. We expect record all these information somewhere in the SDK, so that we can skip the system configuration, and all flashed devices are the same. We know that we can backup the system.img and flash to other devices, but this method cannot help our engineers to develop or release new FW, and it is complicated. So. we expect to modify and record the configurations to the SDK source code.
3.2 now, we use the flash.sh script to flash brand new devices. the console log shows that lots of images are flashed to device, such as mbr.bin, dtb, system.img, etc. we expect to simplify by create a all in one image, so that we could flash only one imge to new device. the image include boot, apps, dtbs, etc.
3.3 last but very inportant, how to flash several new devices at the same time?
FYI
[ 15.9138 ] tegrarcm_v2 --oem platformdetails storage storage_info.bin
[ 15.9144 ] Applet is not running on device. Continue with Bootloader
[ 16.3559 ]
[ 16.3578 ] tegradevflash_v2 --oem platformdetails storage storage_info.bin
[ 16.3583 ] Bootloader version 01.00.0000
[ 16.5796 ] Saved platform info in storage_info.bin
[ 16.5837 ]
[ 16.5837 ] Flashing the device
[ 16.5857 ] tegraparser_v2 --storageinfo storage_info.bin --generategpt --pt flash.xml.bin
[ 16.5864 ]
[ 16.5881 ] tegradevflash_v2 --pt flash.xml.bin --create
[ 16.5886 ] Bootloader version 01.00.0000
[ 16.7951 ] Erasing sdmmc_boot: 3 ......... [Done]
[ 16.8018 ] Writing partition secondary_gpt with gpt_secondary_0_3.bin
[ 16.8028 ] [................................................] 100%
[ 16.8525 ] Erasing sdmmc_user: 3 ......... [Done]
[ 17.8238 ] Writing partition master_boot_record with mbr_1_3.bin
[ 17.8247 ] [................................................] 100%
[ 17.8287 ] Writing partition primary_gpt with gpt_primary_1_3.bin
[ 17.8302 ] [................................................] 100%
[ 17.8339 ] Writing partition secondary_gpt with gpt_secondary_1_3.bin
[ 17.8422 ] [................................................] 100%
[ 17.8546 ] Writing partition mb1 with mb1_prod.bin.encrypt
[ 17.8549 ] [................................................] 100%
[ 17.8615 ] Writing partition mb1_b with mb1_prod.bin.encrypt
[ 17.8838 ] [................................................] 100%
[ 17.8913 ] Writing partition spe-fw with spe_sigheader.bin.encrypt
[ 17.9152 ] [................................................] 100%
[ 17.9231 ] Writing partition spe-fw_b with spe_sigheader.bin.encrypt
[ 17.9578 ] [................................................] 100%
[ 17.9648 ] Writing partition mb2 with nvtboot_sigheader.bin.encrypt
[ 17.9973 ] [................................................] 100%
[ 18.0061 ] Writing partition mb2_b with nvtboot_sigheader.bin.encrypt
[ 18.0468 ] [................................................] 100%
[ 18.0556 ] Writing partition mts-preboot with preboot_d15_prod_cr_sigheader.bin.encrypt
[ 18.1010 ] [................................................] 100%
[ 18.1063 ] Writing partition mts-preboot_b with preboot_d15_prod_cr_sigheader.bin.encrypt
[ 18.1587 ] [................................................] 100%
[ 18.1652 ] Writing partition SMD with slot_metadata.bin
[ 18.2222 ] [................................................] 100%
[ 18.2514 ] Writing partition SMD_b with slot_metadata.bin
[ 18.2571 ] [................................................] 100%
[ 18.2616 ] Writing partition VER_b with emmc_bootblob_ver.txt
[ 18.2638 ] [................................................] 100%
[ 18.2815 ] Writing partition VER with emmc_bootblob_ver.txt
[ 18.3301 ] [................................................] 100%
[ 18.3348 ] Writing partition master_boot_record with mbr_1_3.bin
[ 18.3381 ] [................................................] 100%
[ 18.3419 ] Writing partition APP with system.img
[ 18.3431 ] [................................................] 100%
[ 333.4695 ] Writing partition mts-bootpack with mce_mts_d15_prod_cr_sigheader.bin.encrypt
[ 333.5218 ] [................................................] 100%
[ 333.6643 ] Writing partition mts-bootpack_b with mce_mts_d15_prod_cr_sigheader.bin.encrypt
[ 333.6695 ] [................................................] 100%
[ 333.7729 ] Writing partition cpu-bootloader with cboot_sigheader.bin.encrypt
[ 333.7777 ] [................................................] 100%
[ 333.7918 ] Writing partition cpu-bootloader_b with cboot_sigheader.bin.encrypt
[ 333.7975 ] [................................................] 100%
[ 333.8122 ] Writing partition bootloader-dtb with tegra186-quill-p3310-1000-c03-00-base_sigheader.dtb.encrypt
[ 333.8196 ] [................................................] 100%
[ 333.8447 ] Writing partition bootloader-dtb_b with tegra186-quill-p3310-1000-c03-00-base_sigheader.dtb.encrypt
[ 333.8497 ] [................................................] 100%
[ 333.8633 ] Writing partition secure-os with tos-trusty_sigheader.img.encrypt
[ 333.8723 ] [................................................] 100%
[ 333.8986 ] Writing partition secure-os_b with tos-trusty_sigheader.img.encrypt
[ 333.9059 ] [................................................] 100%
[ 333.9219 ] Writing partition eks with eks_sigheader.img.encrypt
[ 333.9299 ] [................................................] 100%
[ 333.9443 ] Writing partition adsp-fw with adsp-fw_sigheader.bin.encrypt
[ 333.9463 ] [................................................] 100%
[ 333.9690 ] Writing partition adsp-fw_b with adsp-fw_sigheader.bin.encrypt
[ 333.9728 ] [................................................] 100%
[ 333.9802 ] Writing partition bpmp-fw with bpmp_sigheader.bin.encrypt
[ 333.9839 ] [................................................] 100%
[ 334.0199 ] Writing partition bpmp-fw_b with bpmp_sigheader.bin.encrypt
[ 334.0304 ] [................................................] 100%
[ 334.0492 ] Writing partition bpmp-fw-dtb with tegra186-a02-bpmp-quill-p3310-1000-c04-00-te770d-ucm2_sigheader.dtb.encrypt
[ 334.0628 ] [................................................] 100%
[ 334.1004 ] Writing partition bpmp-fw-dtb_b with tegra186-a02-bpmp-quill-p3310-1000-c04-00-te770d-ucm2_sigheader.dtb.encrypt
[ 334.1120 ] [................................................] 100%
[ 334.1334 ] Writing partition sce-fw with camera-rtcpu-sce_sigheader.img.encrypt
[ 334.1433 ] [................................................] 100%
[ 334.1573 ] Writing partition sce-fw_b with camera-rtcpu-sce_sigheader.img.encrypt
[ 334.1610 ] [................................................] 100%
[ 334.1687 ] Writing partition sc7 with warmboot_wbheader.bin.encrypt
[ 334.1729 ] [................................................] 100%
[ 334.1780 ] Writing partition sc7_b with warmboot_wbheader.bin.encrypt
[ 334.1804 ] [................................................] 100%
[ 334.1860 ] Writing partition BMP with bmp.blob
[ 334.1986 ] [................................................] 100%
[ 334.2122 ] Writing partition BMP_b with bmp.blob
[ 334.2163 ] [................................................] 100%
[ 334.2255 ] Writing partition recovery with recovery_sigheader.img.encrypt
[ 334.2292 ] [................................................] 100%
[ 336.8690 ] Writing partition recovery-dtb with tegra186-quill-p3310-1000-c03-00-base.dtb_sigheader.rec.encrypt
[ 336.8731 ] [................................................] 100%
[ 336.8900 ] Writing partition kernel-bootctrl with kernel_bootctrl.bin
[ 336.9044 ] [................................................] 100%
[ 336.9255 ] Writing partition kernel-bootctrl_b with kernel_bootctrl.bin
[ 336.9273 ] [................................................] 100%
[ 336.9313 ] Writing partition kernel with boot_sigheader.img.encrypt
[ 336.9329 ] [................................................] 100%
[ 336.9824 ] Writing partition kernel_b with boot_sigheader.img.encrypt
[ 336.9925 ] [................................................] 100%
[ 337.0156 ] Writing partition kernel-dtb with kernel_tegra186-quill-p3310-1000-c03-00-base_sigheader.dtb.encrypt
[ 337.0276 ] [................................................] 100%
[ 337.0513 ] Writing partition kernel-dtb_b with kernel_tegra186-quill-p3310-1000-c03-00-base_sigheader.dtb.encrypt
[ 337.0593 ] [................................................] 100%
[ 337.0781 ]
[ 337.0963 ] tegradevflash_v2 --write BCT br_bct_BR.bct
[ 337.0993 ] Bootloader version 01.00.0000
[ 337.3032 ] Writing partition BCT with br_bct_BR.bct
[ 337.3039 ] [................................................] 100%
[ 337.3743 ]
[ 337.3986 ] tegradevflash_v2 --write MB1_BCT mb1_cold_boot_bct_MB1_sigheader.bct.encrypt
[ 337.4039 ] Bootloader version 01.00.0000
[ 337.6117 ] Writing partition MB1_BCT with mb1_cold_boot_bct_MB1_sigheader.bct.encrypt
[ 337.6122 ] [................................................] 100%
[ 337.6898 ]
[ 337.6943 ] tegradevflash_v2 --write MB1_BCT_b mb1_cold_boot_bct_MB1_sigheader.bct.encrypt
[ 337.6969 ] Bootloader version 01.00.0000
[ 337.9040 ] Writing partition MB1_BCT_b with mb1_cold_boot_bct_MB1_sigheader.bct.encrypt
[ 337.9044 ] [................................................] 100%
[ 337.9627 ]
[ 337.9627 ] Flashing completed
[ 337.9628 ] Coldbooting the device
[ 337.9660 ] tegradevflash_v2 --reboot coldboot
[ 337.9678 ] Bootloader version 01.00.0000
[ 338.1763 ]
*** The target t186ref has been flashed successfully. ***
Reset the board to boot from internal eMMC.